Sponsored by Splunk
Sponsored by Splunk
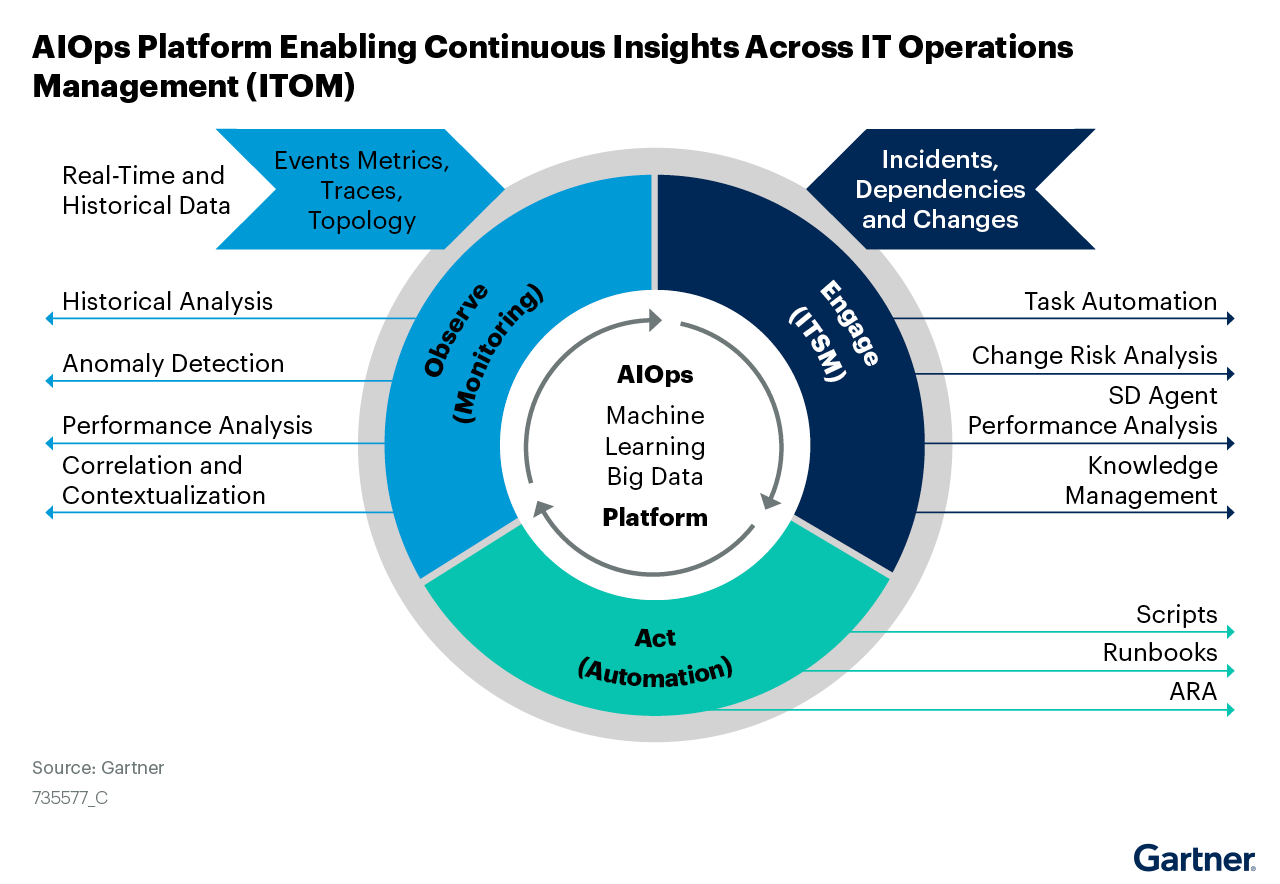
Gartner Market Guide for AIOps Platforms
Sponsored by ServiceNow
Automation Antidotes for the Top Poisons in Cybersecurity Management
Sponsored by Sophos
Checklist: How to stop Ransomware In Its Tracks
Sponsored by Sophos
Is your Endpoint Security the Right One?
Sponsored by Cyberark
Centrally Manage and Secure RPA Deployments with CyberArk and UiPath
Sponsored by Cyberark
The CISO View - Protecting Privileged Access in Robotic Process Automation
Sponsored by Cyberark
Buyers Guide to Identity and Access Management Solutions in a Zero Trust Era
Sponsored by Cyberark
The New Face of Identity and Access Management
Sponsored by Cyberark
Secure your transformational initiatives against modern security threats
Sponsored by Adlumin
The Importance of Proactive Security
Sponsored by Splunk
Splunk IT and Observability Predictions 2022
Sponsored by Splunk
5 Big Myths of AI and Machine Learning Debunked
Sponsored by Splunk