Data Loss Prevention (DLP) , Governance & Risk Management
Report: Shadow Brokers Leaks Trace to NSA Insider
Experts Contend Dumps Are Russia Attempting to Distract From Election Meddling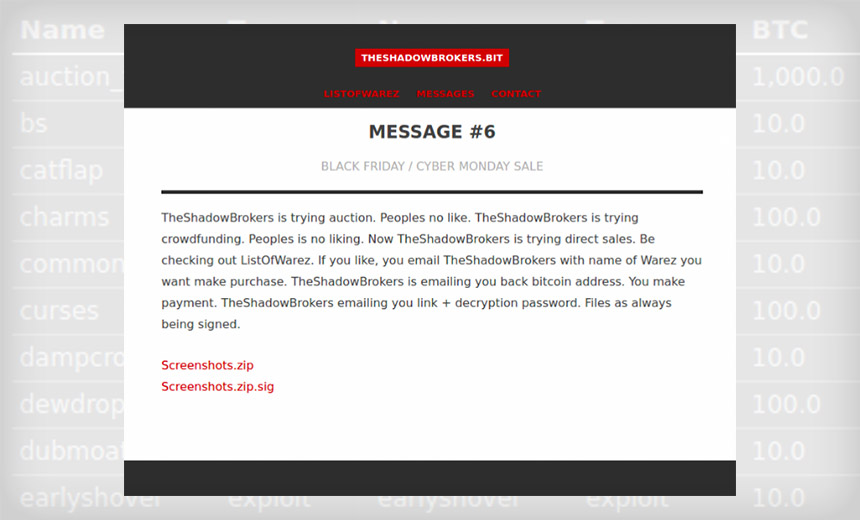
Security experts say a recent Shadow Brokers leak and associated communications appear designed to deflect attention from Russia's alleged meddling in this year's U.S. presidential election. But the latest leak also suggests that a rogue insider at the U.S. National Security Agency may have originally stolen the tools, they warn.
See Also: Live Webinar | Healthcare's Need for Shifting Security Priorities from Prevention to Detection
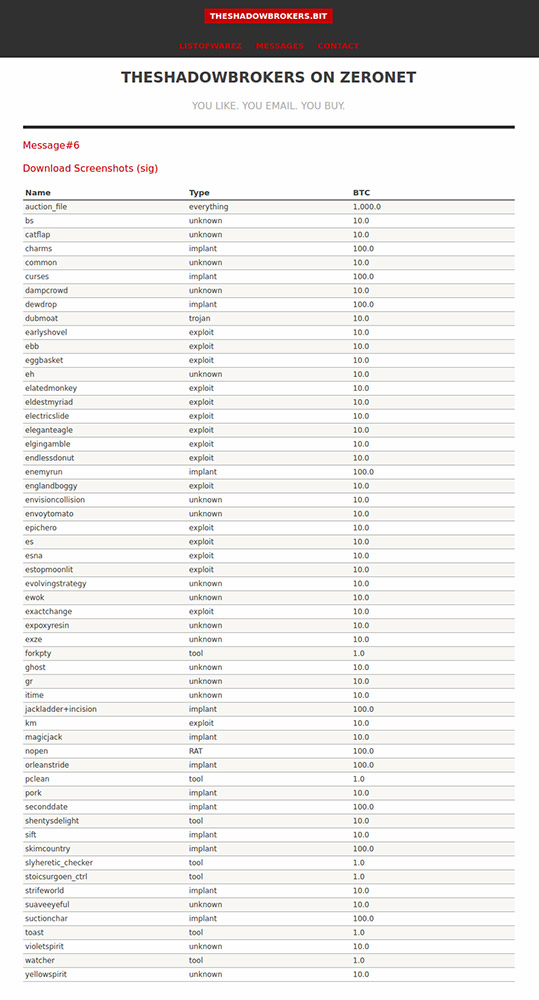
On Dec. 14, the Shadow Brokers group offered multiple new alleged attack tools for sale via ZeroNet, a peer-to-peer encrypted network. The tools include exploits and software implants obtained from the Equation Group, which is the nickname for an advanced hacking group that experts say is likely the NSA's Tailored Access Operations team (see Confirmed: Leaked Equation Group Hacking Tools Are Real).
Many security experts believe that the Shadow Brokers is a Russian intelligence operation being run by the country's internal security service, the FSB, which was formerly the KGB, as part of an information warfare campaign.
The latest tool dump includes hundreds of remote-access tools, exploits and software implants - with names such as "endlessdonut," "englandboggy" and "envoytomato" - as well as related scripts and manuals. Tools are sorted by type, with prices ranging from 1 to 100 bitcoins - currently worth approximately $8,000 to $80,000. Individually, buying all of the tools on offer would cost 1,400 bitcoins - currently worth $1.1 million -although they were also being offered as a complete set for 1,000 bitcoins, or about $800,000.
Profit Motive Questioned
One unanswered question, however, is how did the Shadow Brokers group obtain tools that appear to have come from the NSA's internal, classified network?
On Aug. 27, the FBI arrested now-former NSA contractor Harold T. Martin III - previously employed by Booz Allen Hamilton - on charges that include the unauthorized removal and retention of classified materials (see NSA Contractor Accused of Taking Top-Secret Documents). Authorities have accused Martin of removing more than 50 terabytes of data. They told The Washington Post in October that Martin is the prime suspect in the Shadow Brokers dumps. But the dumps, all signed with the same PGP key, have continued following his arrest and incarceration.
Whether or not Martin is involved, many clues point to some insider involvement, according to security intelligence firm Flashpoint. Its analysis of the latest set of leaked files found that many are written in Markdown, a lightweight markup language that's designed for making easy-to-read code - typically hosted on an internal code repository - that then gets formatted for final use when required, often via a privately hosted git server.
"Based on the extensive use of markdown, the Shadow Brokers more than likely obtained the stolen information through a rogue insider; the documents appear to have been copied from an internal system or code repository and not directly accessed through external remote access or discovered on any external staging server," according to a Dec. 19 blog post published by Flashpoint analysts Ronnie Tokazowski and Vitali Kremez.
"Insiders with access to sensitive information can cause extensive damage, as Edward Snowden proved in June 2013," they add. "While the timeline of events shows that this is not directly related to Snowden, the close proximity of events raises the question if there were multiple insiders acting independently during 2013."
The researchers also don't believe that the Shadow Brokers has suddenly released these files in an attempt to turn a profit. "If the Shadow Brokers were trying to make a profit, the exploits would have been offered shortly after July 2013, when the information would have been most valuable."
Clues Suggest FSB Operation
Some security experts say the Shadow Brokers dumps are notable because they show the FSB not shying away from announcing that it's in possession of NSA attack tools. But simultaneous operations have included the Russian APT group Fancy Bears attempting to plant news stories relating to the Russian doping scandal as well as attempts by a new actor named "Boceffus Cleetus" to plant a bogus story about a shadow war between the CIA and NSA that's being covered up by the U.S. government.
"Russian doctrine is generally about overwhelming the opposition," the operational security expert known as the Grugq says in a three-part analysis of the latest Shadow Brokers dump, published to Medium (see Top 10 Data Breach Influencers).
"I see an overwhelming attempt to get additional narratives into the news cycle ... intended to bleed attention away from the current fixation on Russia's cyber meddling with U.S. elections," he adds (see Obama Suggests Putin Behind Hacks to Influence Vote).
Fake News Shout-Out
The latest tool dump offers multiple clues to support that theory. For starters, the dump was announced via a Dec. 14 post to Medium - "Are the Shadow Brokers selling NSA tools on ZeroNet?" - from a newly registered account in the name of "Boceffus Cleetus."
"I don't wanna be getting arrested for passing on fake news and all," Cleetus wrote. "I rekon (sic) I ain't no security professional but ... I figured y'all might enjoy something I found on the ole Zero Nets. Those dastardly ole shadow brokers have themselves a zite on ZeroNet. Yep and fars as I can tell they appears to be sellin NSA tools individually now."
I just published "Are the Shadow Brokers selling NSA tools on ZeroNet?" https://t.co/sSDrGTcGdK
— Boceffus Cleetus (@CleetusBocefus) December 14, 2016
Enter 'The Dukes of Hazzard'
The Grugq says the message demands a close reading because it's packed with "a huge amount of clever references," starting with the moniker. Bocephus, he notes, is a reference to a ventriloquist dummy, while Cleetus suggests Deputy Cletus Hogg on the TV show "The Dukes of Hazzard," who was known for chasing the Dukes and generally making their life difficult.
That, in turn, appears to be a reference to "the Dukes," which is the name some security firms use for the group that security researchers have nicknamed Cozy Bear, aka CozyDuke or APT 29. That group, sometimes employing the moniker "Guccifer 2.0," has been accused of hacking into the Democratic National Committee's systems as well as the Republican National Committee's systems. And it's been blamed for dumping DNC information in the run up to this year's presidential election, as well as feeding it to WikiLeaks.
Then there's the opening of the Cleetus message: "... this is for the people of the sun!" As the Grugq notes, that's a line from a Rage Against the Machine song - on an album called "Evil Empire" - about Mexicans battling colonial oppressors, in what seems to be an obvious reference to the rhetoric of President-elect Donald Trump.
Based on those - and even more - references, the Grugq says the Shadow Brokers tool dumps appear to be an attempt at distraction.
"This operation (Shadow Brokers dropping info), and the parallel operations (Fancy Bears hack team chasing media; the Cleetus account chasing media) are probably coordinated information operations to attempt to shift attention away from Russia's election meddling," the Grugq says.






















