Anti-Phishing, DMARC , Cyberwarfare / Nation-State Attacks , Email Threat Protection
Lazarus Using Windows Update, GitHub to Deploy Malware
Campaign Targets Job-Seekers; GitHub Used for Command-and-Control Communication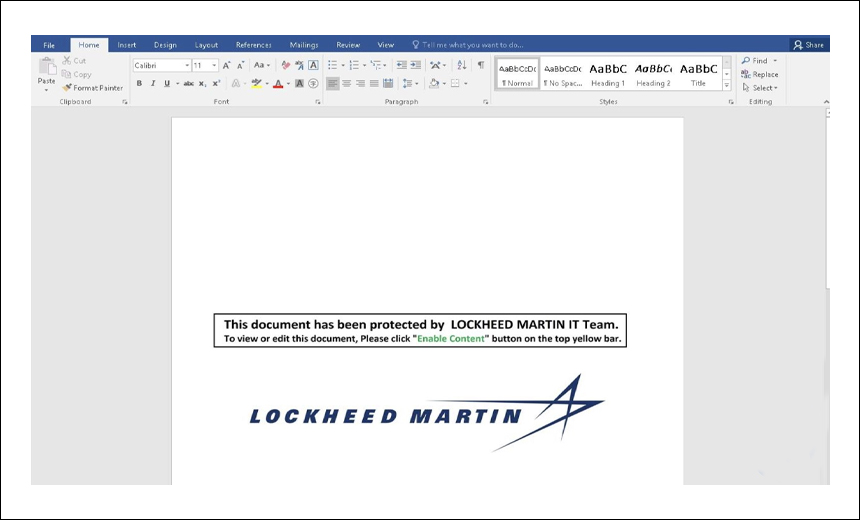
North Korean advanced persistent threat group Lazarus has emerged with a fresh spear-phishing campaign that exploits Windows Updates to execute a malicious payload, using GitHub as a command-and-control server.
See Also: 10 Incredible Ways You Can Be Hacked Through Email & How To Stop The Bad Guys
Researchers at security company Malwarebytes found that Lazarus - an entity sanctioned by the U.S. and the United Nations and tied to North Korea's primary intelligence agency, the Reconnaissance General Bureau - conducted spear-phishing attacks weaponized with malicious documents that use known job opportunities as the theme. The researchers identified two decoy documents masquerading as American global security and aerospace giant Lockheed Martin.
The Lazarus Group is known for targeting the defense industry and for updating its toolset to evade security mechanisms. Since its inception in 2009, the group has reportedly been responsible for many high-profile attacks, such as the 2014 Sony breach and Wannacry, as well as more recent financially motivated attacks, gaining worldwide attention.
The Malwarebytes Threat Intelligence team says it is actively monitoring Lazarus activities and was able to spot a new campaign on Jan. 18, 2022.
The Malwarebytes team attributes this activity to Lazarus based on its attack techniques and because the malicious document’s metadata used in this campaign links it to several other documents used by this actor in the past.
Campaign Uncovered
Researchers at Malwarebytes uncovered that the two macro-embedded documents were luring victims with new job opportunities at aerospace firm Lockheed Martin.
The malicious documents named Lockheed_Martin_JobOpportunities.docx and Salary_Lockheed_Martin_job_opportunities_confidential.doc were first made in April 2020.
"But we have enough indicators that confirm that they have been used in a campaign around late December 2021 and early 2022. Some of the indicators that show this attack operated recently are the domains used by the threat actor," the researchers say.
They also say that the malicious documents use the same attack theme and have common features, such as using embedded macros, but they say that the full attack chain is totally different.
"Throughout 2021, North Korea-associated threat groups posed as security researchers to target cybersecurity practitioners. In a separate campaign in November 2021, North Korea-linked 'ZINC' APT group posed as recruiters from Samsung to target employees at the security firms," says Xueyin Peh, senior cyber threat intelligence analyst at Digital Shadows.
Peh says that the impersonation of Lockheed Martin in the latest campaign could suggest that the North Korean regime is after defense-related information.
"With the popularity of supply chain attacks among APT groups, it is also possible that this latest campaign sought to target the wider defense sector, and likely governments, when considering the close connections between these two industries," Peh says.
"Cybercriminals use emotional manipulation in their malware campaigns, fully aware that victims are more likely to respond to an 'urgent' or 'exciting' message. This attack is no exception; by boasting coveted job opportunities, like this one with Lockheed Martin, the likelihood that the victim will click on the included malicious links in a moment of heightened emotion is increased," says Magni Reynir Sigurðsson, senior manager of detection technologies at Cyren.
Sigurðsson says the technique used by Lazarus in this attack is particularly devious, because by executing its malicious code through the Microsoft Windows Update client, GitHub, antivirus software is efficiently evaded. But malware campaigns using Office documents with embedded malicious macros have been ongoing for many years now, he says, and organizations must make sure that Office tools - such as Word, Excel and PowerPoint - have macros disabled by default. They must also educate their employees and users to never to enable macros in documents unless they are 100% sure of the origin of the document and that it is 100% safe, Sigurðsson says.
Although the group has used its old job theme method, researchers say they found several new techniques used to bypass detections. They include:
- KernelCallbackTable: Helps hijack the control flow and shellcode execution;
- Windows Update client: Enables malicious code execution;
- GitHub: Enables command-and-control communication.
Attack Analysis
The initial attack vector executed malicious macros embedded in the malicious Word document, which performs a series of injections and achieves startup persistence in the target system.
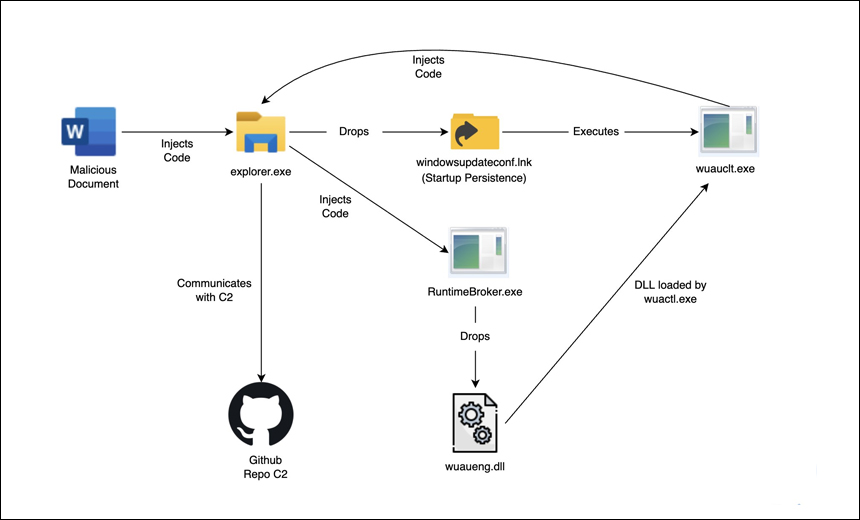
During the attack, the malware uses a code that researchers say is unusual, along with lesser-known techniques, to hijack the control flow and execute malicious code.
"The malware retrieves the address of the 'WMIsAvailableOffline' function from 'wmvcore.dll', then it changes the memory protection permissions for code in 'WMIsAvailableOffline' and proceeds to overwrite the code in memory with the malicious base64 decoded shell-code," the researchers say. "Another interesting thing happening in the code is the control flow hijacking through the KernelCallbackTable member of the PEB. A call to NtQueryInformationProcess is made with ProcessBasicInformation class as the parameter which helps the malware to retrieve the address of PEB and thus retrieving the KernelCallbackTable pointer."
The researchers say that the KernelCallbackTable feature is initialized to an array of callback functions when user32.dll is loaded into memory, and these functions are used whenever a graphical call is made by the process.
In order to hijack the control flow, however, an attacker using this malware replaces the USER32!_fnDWORD callback in the table with the malicious WMIsAvailableOffline function.
The researchers say that once this flow has been hijacked and the malicious code has been executed, the code restores the KernelCallbackTable to its original state.
Once the DLL has been loaded and executed inside the explorer.exe process, "it mainly drops the LNK file (WindowsUpdateConf.lnk) into the startup folder and then it checks for the existence of wuaueng.dll in the malicious directory and manually loads and executes it from the disk if it exists" in the C:Windowssystem32 folder, according to the researchers.
"This is an interesting technique used by Lazarus to run its malicious DLL using the Windows Update Client to bypass security detection mechanisms. With this method, the threat actor can execute its malicious code through the Microsoft Windows Update client by passing the following arguments: /UpdateDeploymentProvider, Path to malicious dll and /RunHandlerComServer argument after the dll," the researchers say.
When they analyzed the second document, the researchers found that the initial attack vector was the same as for the first document, but the malware dropped by the macro was different.
"This document also uses KernelCallbackTablem to hijack the control flow just like our first module; the injection technique used by the shellcode also resembles the first document. The major difference in this document is that it tries to retrieve a remote HTML page and then executes it using mshta.exe. The remote HTML page is located at https[:]//markettrendingcenter[.]com/member.htm and throws a 404 Not Found which makes it difficult for us to analyze this document any further," the researchers say.
Group's First Use of GitHub
The researchers spotted that the malware was using GitHub as command and control (C2) and that Lazarus was using it for the first time.
"Using Github as a C2 has its own drawbacks but it is a clever choice for targeted and short-term attacks as it makes it harder for security products to differentiate between legitimate and malicious connections," the researchers say.
While analyzing the core module, the researchers were able to get the required details to access the C2 but unfortunately it had already been cleaned and they were not able to get much, except one of the additional modules loaded by the core_module.dll remotely.
"TTPs used in these attacks showed little deviation. Phishing and spear-phishing, using job opportunities as lures continue to be used. The abuse of GitHub is also not novel among APT groups and constitutes 'living off the land' techniques, in which threat actors use legitimate infrastructure to avoid detection. Spotting suspicious emails and refraining from interacting with the content would remain the first line of defense when mitigating such attacks," Peh says.
"Current email security is focused primarily on prevention, but still every single day consumers and businesses alike are falling victim to devious targeted malware attacks like this one," Sigurðsson says. He says companies need to implement a robust, layered security strategy that includes real-time detection of zero-day and unique phishing threats and that adding real-time detection and automated remediation capability to identify and eliminate threats rapidly will minimize the impact when a malicious email does makes it through.
Recent Lazarus Activities
Blockchain security firm Chainalysis earlier this month said that the North Korean regime's state-backed hackers lifted nearly $400 million in cryptoassets last year - hitting investment firms and centralized exchanges (see: North Korean Crypto Theft Totals $400 Million in 2021).
New data on the Lazarus Group and other RGP-linked activity comes on the heels of another warning from the cybersecurity and antivirus firm Kaspersky, which last week said the North Korea-backed gang BlueNoroff is now targeting small and midsized cryptocurrency startups in a campaign called "SnatchCrypto" (see: North Korean APTs Target Cryptocurrency Startups).
In October 2021, the group was also reported to be developing supply chain attack capabilities using its multiplatform malware framework, MATA, for cyberespionage goals (see: Lazarus Adds Supply Chain Attack to List of Capabilities).