Access Management , Cybercrime , Fraud Management & Cybercrime
Credential-Stuffing Attacks Affect Canadian Services
Government Investigating 2 Incidents That Targeted Thousands of Accounts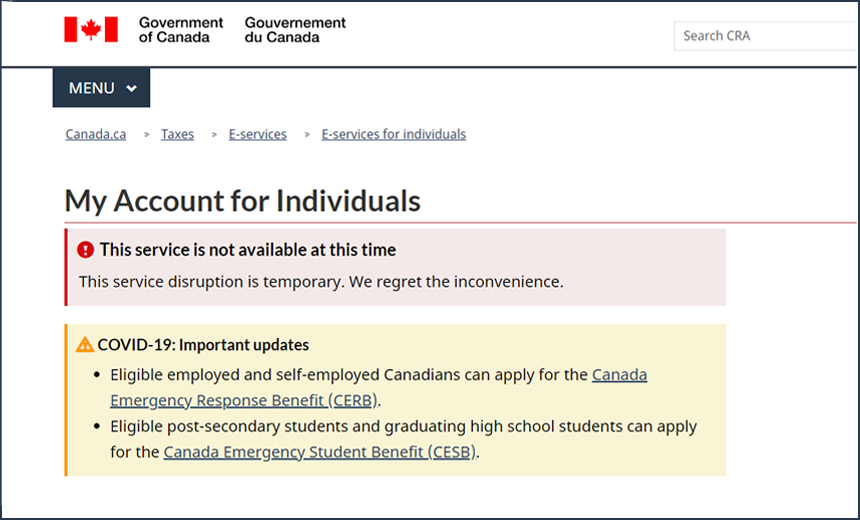
The Canadian government is investigating two security incidents that affected some of the country's most essential services, including taxation, healthcare, welfare benefits and immigration.
See Also: The State of Organizations' Security Posture as of Q1 2018
In both cases, it appears that hackers used credential-stuffing techniques to guess the usernames and passwords of Canadian citizens in an attempt to fraudulently access various government services and funds, according to a statement issued Saturday by Marc Brouillard, acting CIO of the Candian government.
Credential stuffing refers to how attackers use lists of compromised authentication credentials to crack into accounts, hoping credentials were reused for many sites.
Canadian authorities have not determined if any personal information has been breached or if the hackers successfully accessed any of the government benefit services. The Royal Canadian Mounted Police are investigating, along with other agencies.
As of Monday, the sign-on page for the Canada Revenue Agency remained offline because the government shut the site down to conduct a further investigation, according to a Monday update.
Affected Services
In one attack, the hackers attempted to breach the government's GCKey service - a single sign-on system used by Canadian citizens to access about 30 government services offered by Canada's employment and social welfare agency and the department that oversees immigration.
Of the approximately 12 million active GCKey service accounts used by citizens in Canada, government officials believe about 9,000 were targeted by this one credential-stuffing attack.
The CBC news service reported the government’s precautionary shutdown of these sites over the weekend meant that citizens likely found it more difficult to apply for emergency COVID-19 benefits.
In addition to the attack that affected the GCKey service, authorities are investigating a second incident that targeted 5,500 citizen accounts associated with the Canada Revenue Agency, which administers the country's tax laws.
Canadian citizens can use either a separate sign-on page to access their Canada Revenue Agency accounts or the GCKey service, according to the government statement.
"Approximately 5,500 CRA accounts were targeted as part of the GCKey attack and another recent ‘credential stuffing’ attack aimed at the CRA," the statement notes. "Access to all affected accounts has been disabled to maintain the safety and security of taxpayers’ information, and the agency is contacting all affected individuals and will work with them to restore access to their CRA MyAccount."
Some of those affected by these two security incidents have expressed frustration at the Canadian government's response. Leah Baverstock, a law clerk in Ontario, found that her Canada Revenue Agency account had been hacked earlier this month and someone attempted to sign her up for COVID-19 benefits.
"The lady I spoke to at CRA said: 'This is a one-off,"' Baverstock told the Canadian Press news service on Sunday. "And she told me a senior officer would be calling me within 24 hours because my account was completely locked down. And I still haven't heard from anybody."
In Monday's update, Brouillard noted that the government is conducting a wide-ranging investigation of what happened and who has been affected.
"We're constantly evaluating our security posture. … this is an ongoing challenge. This is not a hacker trying to go through a backdoor," Brouillard says. "They are going through the system like normal users … and it is hard to detect that. We have systems in place to monitor these behaviors. That is when this particular attack was identified."
Since the start of the COVID-19 pandemic, Canada has faced many of the same cyber problems as the U.S. has with increases in attacks such as credential stuffing, says Imran Ahmad, a Toronto-based attorney who is a partner at Blake, Cassels & Graydon LLP and specializes in technology, cybersecurity and privacy law.
"We have definitely seen an uptick in cyber criminals using various techniques, including credential stuffing, exploiting exposed remote desktop protocols and sophisticated phishing attacks during the current pandemic," Ahmad tells Information Security Media Group. "Their goal being to exploit vulnerabilities in the remote working model and conduct financial fraud, such as fraudulent wire transfers."
Credential Stuffing
In a December 2019 interview, Troy Hunt, creator of the Have I Been Pwned data breach notification service, noted that the success of credential stuffing raises questions about the controls that companies have in place to ensure that someone who has the right username and password for a service - but is not actually the legitimate user - is denied access (see: How Can Credential Stuffing Be Thwarted?).
Tim Wade, the technical director of the CTO team at security firm Vectra, notes that by reusing the same passwords, users expose themselves to credential-stuffing attacks.
"Credentials may be harvested as part of a breach and subsequently monetized," Wade tells ISMG. "The risks around credential theft are compounded by the relatively common practice of credential reuse, where a breach in one platform may affect another unrelated platform due to users reusing their credentials."
Managing Editor Scott Ferguson contributed to this report.