Fraud Management & Cybercrime , Ransomware
Australia Faces Consequences of Standing Up to Ransomware
Also: Ransomware Gang Leaks Negotiation Chat With Technical Detail About Attack
The stark consequences of not paying a ransom to a gang of cyber extortionists became painfully clear in Australia this week.
On Tuesday, a ransomware group began releasing some of the data it stole from the systems of Medibank, one of Australia’s largest health insurers. The day before, Medibank publicly announced it would not pay a ransom. (see: Medibank Says No to Paying Hacker's Extortion Demand).
Medibank says the breach affects 9.7 million current and former customers. The data includes claims-related information, including codes for medical diagnoses such as whether a person smokes or may use illegal drugs.
On Thursday, the ransomware gang said it wanted US$10 million - AU$15 million - to not release the data but said it would come down to $9.7 million, which equals $1 for each record. It also released a very sensitive file of records of policyholders that contained medical codes related to abortion.
That has led some to question whether it might have been worth paying the ransom and whether the Medibank incident should not have been used to make a point to the cybercriminal world. Paying, however, would contradict Australian government advice.
Deterrence is built up over time and isn't going to form as a result of a reaction to one incident. Given the nature of the data, this one stands out. And the choice to not pay does as well. It does send a message, but one that painfully affects 9.7 million people.
Medibank counts the country's prime minister - and ironically, its cybersecurity minister - as customers. Its data breach and subsequent extortion have caused the country to take a hard look at whether its laws are strong enough to protect personal data.
Minister for Home Affairs and Cyber Security Clare O'Neil told Parliament on Wednesday: "I cannot articulate the disgust I have for the scumbags who are at the heart of this criminal act. People are entitled to keep their health information private."
"Even amongst ransomware attackers, the idea of releasing personal medical information of other people is considered beyond the pale. So make no mistake about it: This is not just any ordinary group of scummy criminals. This is the lowest of the low."
I know many are anxious about what has happened at Medibank. Here's the latest update on the Medibank cyber incident and how the Albanese Government is working to protect Australians. #qt pic.twitter.com/8ZHUMRJZUX
— Clare O'Neil MP (@ClareONeilMP) November 9, 2022
Medibank has said that compromised login credentials led to its data breach. To be clear, we still don't exactly know how those stolen login credentials led to the loss of the personal details of 9.7 million people.
But the attackers have revealed some details in their first batch of data, which included logs of conversations they had with Medibank officials.
In the chat, there is a comment that points to the attackers having VPN access. The attackers then claim they accessed Redshift, an Amazon data warehousing product, via jump servers.
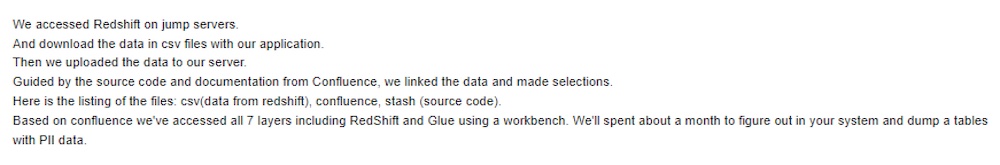
The Medibank attackers, whom some researchers call BlogXX, said they spent a month digging around the health insurer's systems. Eventually, they dumped the SQL database tables containing personally identifiable information and eventually they put that data in .csv files that they supplied to Medibank as proof of the intrusion.
The attackers also claim to have achieved access to Medibank's Confluence server, which is Atlassian's collaboration software, and grabbed source code from Stash, a source code management tool.
Compromised Access Credentials
Medibank did eventually catch the attackers, but only after the gang had stolen the personal data. Late last month, Medibank said it caught the precursors to a ransomware attack and thought no data had been accessed. It seemed to be positive story, but shortly afterward, Medibank told the public that the attackers had in fact stolen data and contacted them, wanting to negotiate.
How did the attackers get the stolen access credentials? I recently spoke with a former Medibank employee whose login credentials turned up on the dark web in August, and an interesting conversation ensued.
For background, login credentials are constantly stolen, bought and sold. "Every org has creds for sale," one source tells me. Medibank is no different. At least a half-dozen Medibank accounts were available for sale in August, according to Los Angeles-based cybersecurity intelligence company Resecurity.
I looked at the credentials and emailed some of the people. One responded, and we spoke on the phone. He was a part-time COVID support officer with Medibank. Policyholders would call in with questions about COVID, and he said he would read COVID guidance from NSW's website.
His Medibank email address and password were for sale along with the URL where those credentials were valid. His data was harvested by the Redline botnet malware, which had apparently infected one of his devices.
But he says he's in disbelief of that as he uses four AV programs and is careful about potentially malicious links. His ANZ bank account ended up locked after hackers went after it, too, in August, but he didn't lose money.
He worked from home and would log into Medibank's systems with his email address and password. Then he'd enter a one-time passcode from the Symantec VIP code generator on his phone. Once in, he had access to Medibank's Patient Flow Portal.
He could see names, addresses, what local health district a person lives in and sometimes disease information relevant to COVID. But he says there was a "limit" to what patient information he could access.
He left Medibank in May, so if Medibank followed good IT security practices, his login credentials should have been revoked then. It's great that Medibank had two-factor authentication in place, but there are various tricks to get around it.
Did this person's account compromise lead to where Medibank is now? Probably not, but it's not out of the realm of possibility, either. Medibank's incident response and forensics investigation may figure out where all of this started and whether it was this account or a different one.
But rather than try to speculate on who is "patient zero," this tale is intended to show the possible malicious path via stolen creds: Malware on work-from-home computer > Harvested login credentials > Access to corporate network > More devious things, depending on what security controls are in place. And then eventually, perhaps, the worst data breach in Australian history.











