Application Security , Incident & Breach Response , Next-Generation Technologies & Secure Development
Backdoor Discovered in US Federal Agency Network
System Control of International Religious Freedom Commission Network Enabled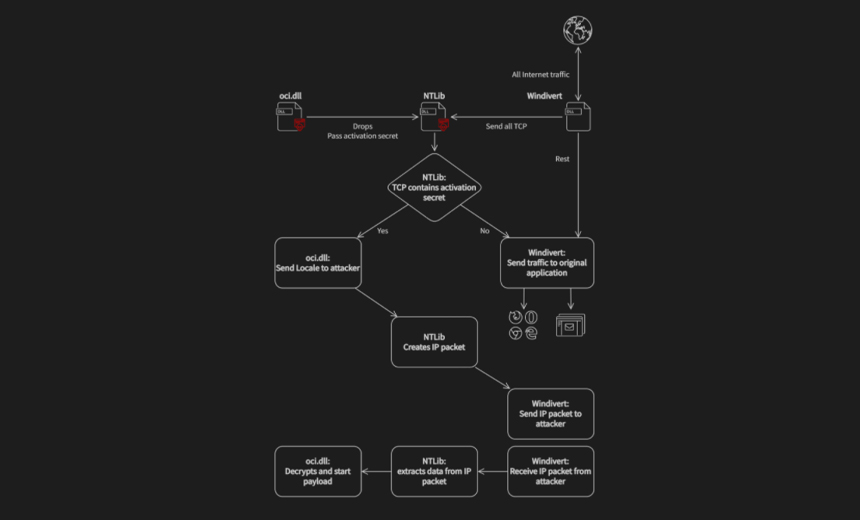
A backdoor in the network of the United States Commission on International Religious Freedom has allowed attackers to intercept, and likely exfiltrate, all local network traffic on the agency's systems, a spokesperson at cybersecurity firm Avast tells Information Security Media Group.
See Also: Panel Discussion | The 2021 Global State of Security
The Czech-based firm has "attempted to reach the agency via multiple channels," the spokesperson says.
"We contacted the agency and spoke to its executive director [Erin D. Singshinsuk] in May. We also reached out to the incident response wing of the federal government over the proper channels, providing all the information we had collected over this case, including a malware sample. CISA was [also] one of the agencies we talked to in order to help us reach the victim, [in June]," the spokesperson tells ISMG.
As there was "no follow up" from the agency for months, however, the security firm says it released its findings in a threat intel blog to raise awareness and allow likely victims to protect themselves based on the very "limited visibility" into the indicators of compromise of the backdoor, Avast says.
Singshinsuk did not respond to ISMG's request for comments.
Lack of Response
Avast's public blog post does not include the identity of the victim organization, as the researchers did not know whether the risk had been mitigated or not, the spokesperson says.
Due to lack of response from the federal agency, the researchers were unable to monitor the specifics of the attack from the back end, and were therefore unable to attribute it to a specific attacker or determine the impact, duration and persistence of the attack.
But based on an analysis of the signatures and information they could gather, the researchers say that the attackers had "total visibility of the network and complete control of a system."
"Based on our analysis of the files in question, we believe it’s reasonable to conclude that the attackers were able to intercept and possibly exfiltrate all local network traffic in this organization," they say.
"This could include information exchanged with other U.S. government agencies and other international governmental and non-governmental organizations focused on international rights. We also have indications that the attackers could run code of their choosing in the operating system’s context on infected systems, giving them complete control," Avast says in the threat intel blog.
The backdoor attack, the researchers say, is just the first step in a multistage attack designed to penetrate this particular organization's network or others networks more deeply.
The Avast spokesperson tells ISMG that "given the very limited visibility, we [Avast researchers] only saw Windows malware in the attack."
Two Malicious Files Discovered
Avast's suspicion of network interception and exfiltration is based on its analysis of two files the researchers obtained. The company did not provide ISMG with the origin of the files.
One of the files, through which the threat actor initiates the backdoor, is termed as a "downloader" by Avast. It masquerades as a legitimate Windows file named oci[.]dll and abuses the WinDivert, a legitimate packet-capturing utility that can be used to implement user-made packet filters, packet sniffers, firewalls, NAT, VPNs, tunneling applications, etc., without the need to write kernel-mode code. This allows the attacker to listen to all internet communication via the victim's network, they say.
"We found this first file disguised as oci.dll ('C:WindowsSystem32oci.dll') - or Oracle Call Interface. It contains a compressed library [called NTlib]. This oci.dll exports only one function 'DllRegisterService.' This function checks the MD5 of the hostname and stops if it doesn’t match the one it stores. This gives us two possibilities. Either the attacker knew the hostname of the targeted device in advance or the file was edited as part of the installation to run only on an infected machine to make dynamic analysis harder," the researchers say.
The NTlib contains a set of export functions, each of which has a secret activation argument that acts as an authentication. The only interesting function in this export function set, according to the researchers, is the NTAcceptPWD.
"[It] gets an activation secret as an argument and sniffs all the incoming TCP communication, searching for communication with that activation secret. It means that the malware itself does not open any port on its own, it uses the ports open by the system or other applications for its communication. The malicious communication is not reinjected to the Windows network stack, therefore the application listening on that port does not receive it and doesn’t even know some traffic to its port is being intercepted," the researchers say.
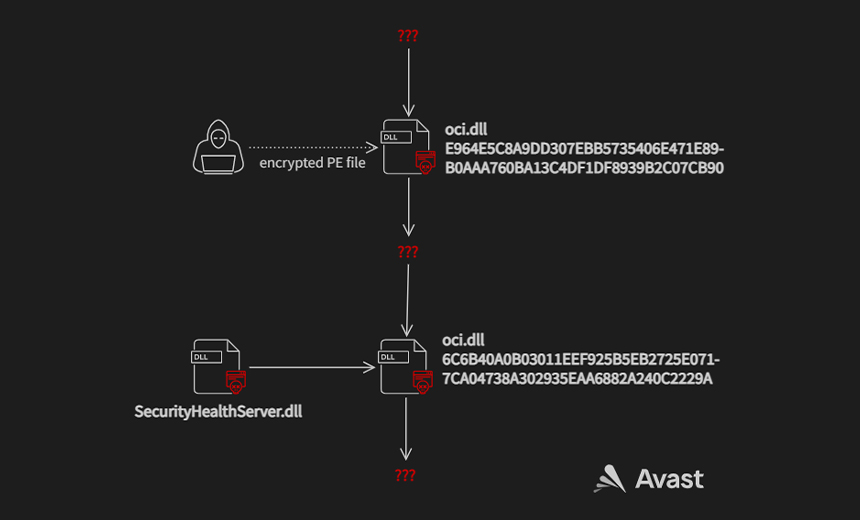
The second file, which the researchers call "decryptor," replaces the first fake oci[.]dll downloader at a later stage with a code that decrypts a malicious file named SecurityHealthServer.dll and loads it into memory.
The analysis of this second file led the researchers to link it to another identical malicious file - rcview40u[.]dll - that was used in an espionage campaign targeted at South Korean organizations in 2018, reported by Trend Micro.
Barring a few changes, such as starting the decrypted file in a new thread instead of in a function call - which is what rcview40u.dll does - "this oci[.]dll exports same functions as rcview40u[.]dll," the researchers say.
They verified their findings of the malicious oci[.]dll files by starting the calculator on an infected machine over the network with a Python script that they uploaded on GitHub.
Other Agencies Alerted
Avast has alerted other government and nongovernment agencies focused on international rights to check for indicators of compromise, the spokesperson tells ISMG.
"We recommend agencies and organizations to look at the IoCs we covered in our post, and specifically for any indications of abuse of the WinDivert library, as explained in our post," the Avast spokesperson says.














